How the Kochava Foundry team uncovered an install farm for a fintech company
Fraud isn’t always blatantly obvious at first but can creep into campaigns, hiding in plain sight as good traffic. Thankfully it does, however, always leave a trail. Real-time mitigation solutions stop the lion’s share of fraud from the most common tactics, but marketers need to remain vigilant of data anomalies nonetheless—although they don’t immediately signal fraud, it pays to have experts dig in. If something stands out as different or strange in your data, don’t let it go. It could be an indicator of a much larger fraud being committed.
That’s exactly what happened to a fintech services app running a large campaign in EMEA, and it all started with a grouping of fake emails linked back to what had appeared to be a successful acquisition campaign. The fintech marketing team contacted Kochava FoundryTM to determine the cause, but how the Foundry analyst investigated may surprise you.
The anatomy of a fraud investigation: First, attempt to explain anomalies
When presented with an anomaly, Kochava Foundry analysts do not immediately suspect fraud because if initially set on proving fraud without much evidence, that could cloud the investigation and overlook simple data errors or alternative explanations.
In the case of this fintech company, our analyst first worked on the assumption that the campaign traffic was legitimate (innocent until proven guilty) and sought potentially reasonable explanations for the anomalies. Developer testing, event tracking implementation issues, and other errors were reviewed and eliminated as potential causes.
Next, the analyst looked at the app’s traffic during the campaign. The campaign was running on a cost-per-engagement (CPE) model, and it drove an impressive amount of signups, the target event. As the analyst probed further, he saw a disproportionate number of the signups within the campaign time frame had absolutely no subsequent money transfer events. By segmenting the newly acquired audience cohorts by attributed network and sub-publisher, it became clear that the exponential spike in signups with no transfers was isolated to a specific grouping of sub-publishers. While the typical rate of signup-to-no-transfer was 30-40% across most paid and owned media, these cohorts displayed a signup-to-no-transfer rate of 99%. This was a major outlier and highly suspect. It became the first red flag that install farm fraud was likely at play behind these publishers. The hypothesis was that an install farm was clicking campaign offers, quickly installing the app, then completing the target CPE event with a fake email before then uninstalling the app to rinse and repeat the process.
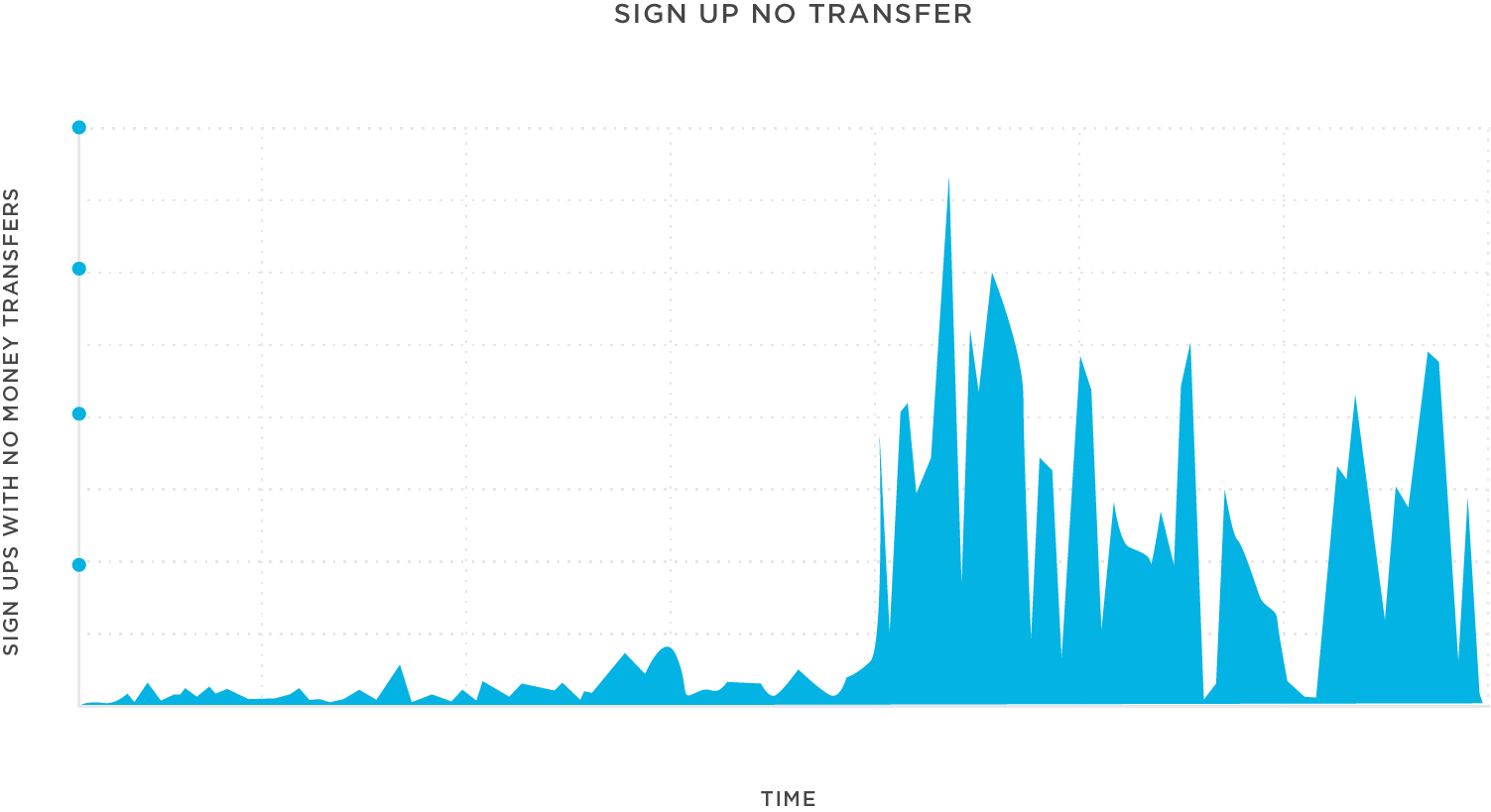
Confirming the tell-tale signs of install farm fraud
Once there is evidence of a type of fraud, in this case, sequenced app activity from an install farm, the Foundry analyst checked for other “confirming symptoms” of that fraud tactic. Among other symptoms, he specifically looked for:
- Outliers in the time-to-install (TTI) distribution between the attributed ad click and first app launch (a.k.a. install)
- Outliers in the time-to-engagement (TTE) distribution, the time between first app launch/install and completion of the signup event
- Abnormally high percentage of older device types and operating systems (OS)
Assessment from multiple angles
Both TTI and TTE were plotted against the device cohort from these sub-publishers alongside the rest of the fintech company’s omni-channel media partners. The distribution from the suspect cohort was strikingly homogeneous (meaning the timing was similar across all converting devices). This is a commonly observed outcome when install farm workers are performing the same rinse & repeat process across racks of devices. On the other hand, other publisher sources displayed a non-homogeneous distribution trend where TTI and TTE naturally varied according to expected human behavior differences.
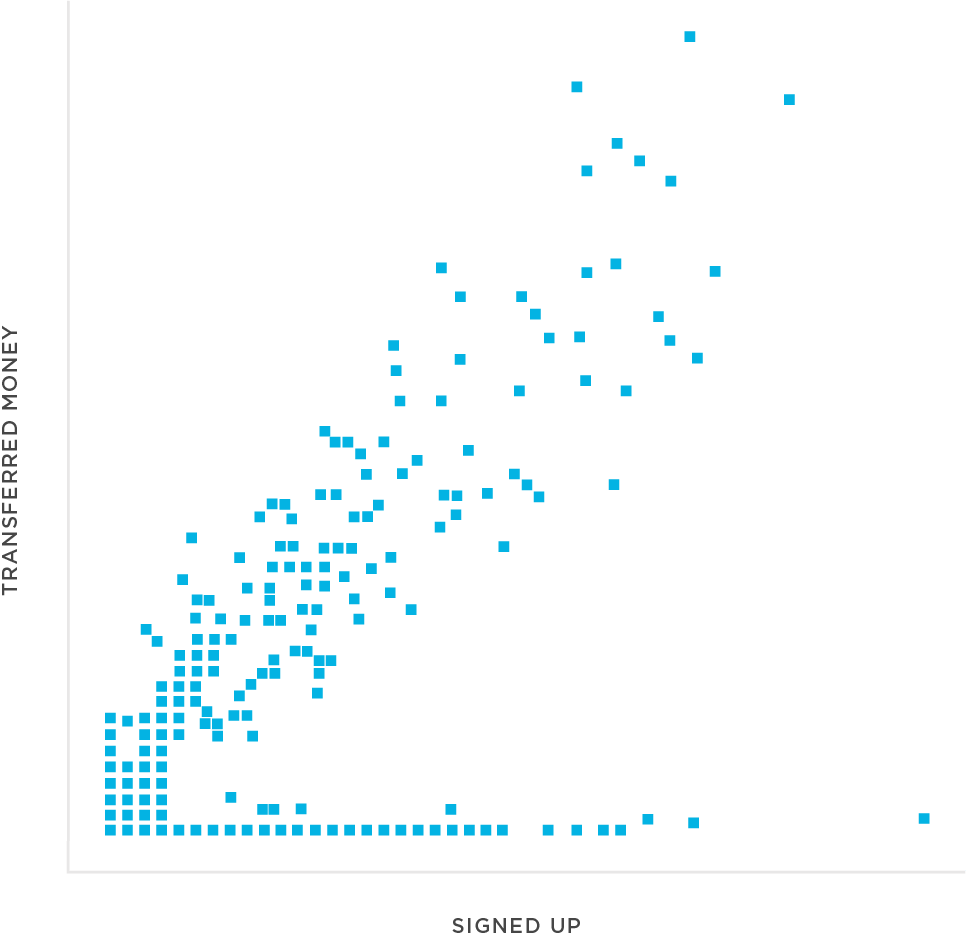
To further confirm that an install farm was at play, the analyst observed the makeup of device type and OS among the suspect cohort. As suspected, the makeup was overwhelmingly older models, whereas the audience from all other publishers had a healthy distribution across new and older devices and OS versions.
These indicators were combined with other proprietary install farm detection methods and solidified the outcome of the Foundry investigation. The Foundry team then advised the fintech marketing team on the next steps to mitigate the issue and secure make-goods from the media partners involved.
Pulling on a thread, but making no assumptions
Most of the time with respect to fraud investigations, the Foundry team is evaluating odd campaign data based on something the client is questioning. In this case, the fintech company saw a set of suspicious-looking emails and asked the team to explore them further. Once the analyst detangled some of the data threads, fraud was the evident culprit.
Real-time anti-fraud tools are necessary and effective, catching the majority of the fraud occurring in the ecosystem. However, marketers must stay vigilant to anything that looks suspicious or even too good to be true. For this fintech app’s campaign, much of the traffic looked normal, and it wasn’t until the traffic was analyzed from different angles to prove its validity that the fraudulent characteristics showed pointing to install farm fraud perpetrated by a subset of publishers.
Want to know how the Foundry team can help you? Request a free consultation.



